Net income. Securities and Exchange Commission.
February Retrieved September 18, Encyclopedia of Cyber Warfare. USA Today. Retrieved May 21, Yahoo Finance. Retrieved November 20, September 20, Retrieved September 22, November 15, Retrieved November 15, IT PRO. The Mercury News. November 28, Business Insider. The New York Times. January 2, Financial Times. CSO Online. August 4, Retrieved July 12, July 1, Sonoran Weekly Review. May 6, Archived from the original on August 10, Retrieved May 6, Ars Technica. Retrieved November 30, Wall Street Journal. Retrieved March 18, Archived from the original on January 31, Retrieved April 12, Retrieved October 15, Retrieved June 21, Washington Post.
The Guardian. The Register. Retrieved September 12, Registered in England and Wales.
Number NASDAQ: FEYE , the intelligence-led security company, today announced several enhancements to its endpoint security solution designed to offer unparalleled protection from threats missed by legacy and next-generation endpoint solutions. These new capabilities are generally available to customers around the world today.
Sophos Next Generation Data Protection: Security Made Simple
Additional enhancements will include industry-leading anti-virus AV capabilities for known malware protection, virtual and cloud form factors, expanded behavioral analysis and machine learning capabilities to protect against unknown malware and exploits, and Linux support for server coverage. This seamless integration of prevention, detection and response capabilities in a single agent also greatly simplifies the customer deployment and lowers the performance impact on the endpoint.
With over a decade of experience responding to some of the largest breaches in the world, we see where other products fail and can codify that intelligence into a comprehensive endpoint solution focused on simplicity and speed. Most importantly, our ability to take threat intelligence and rapidly turn that into new protections and features — such as with recent Shamoon 2. The behavioral analysis engine that powers the new Exploit Guard prevention capability has shown in testing that it can detect and block percent of the previously unknown exploits — without signatures or indicators — that were publicly reported in , , and FireEye Endpoint Security safeguards against the threats missed by legacy and next-generation endpoint security products.
FireEye has entered an OEM relationship with a leading anti-virus solution to deliver customers comprehensive, simplified endpoint protection from threats — known and unknown — to further simplify security operations at no additional cost. This context helps prioritize and triage threats, giving security teams time to focus on more proactive work.
Flame (malware)
The integration of anti-virus is expected to occur during the first quarter of with additional progressive roll-out of other detection and prevention capabilities in the first half of For FireEye Partners, Endpoint Security can replace customer legacy endpoint products with a single agent that addresses compliance requirements. Partners can further differentiate Endpoint Security with FireEye by adding the powerful simplicity of Helix and a "single plane of glass" to process all their security alerts from all their products and focus on what matters most.
FireEye is the intelligence-led security company. With this approach, FireEye eliminates the complexity and burden of cyber security for organizations struggling to prepare for, prevent, and respond to cyber attacks. FireEye has over 5, customers across 67 countries, including more than 40 percent of the Forbes Global This press release contains forward-looking statements, including statements related to the expectations, beliefs, features, capabilities, benefits and availability of FireEye Endpoint Security and enhancements and technologiy integrations with respect thereto, and statements related to opportunities for FireEye and its channel partners.
Get In Touch
These forward-looking statements involve risks and uncertainties, as well as assumptions which, if they do not fully materialize or prove incorrect, could cause the performance of these new platforms and FireEye's results to differ materially from those expressed or implied by such forward-looking statements. All forward-looking statements in this press release are based on information available to the company as of the date hereof, and FireEye does not assume any obligation to update the forward-looking statements provided to reflect events that occur or circumstances that exist after the date on which they were made.
Any future product, service, feature, benefit or related specification that may be referenced in this release is for information purposes only and is not a commitment to deliver any technology or enhancement. FireEye reserves the right to modify future product and services plans at any time. Database Security. Security Monitoring. Advanced Threats. Insider Threats. Vulnerability Management.
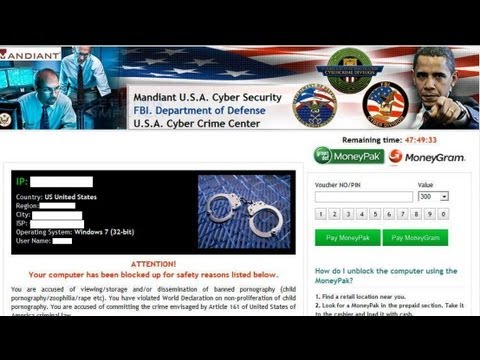
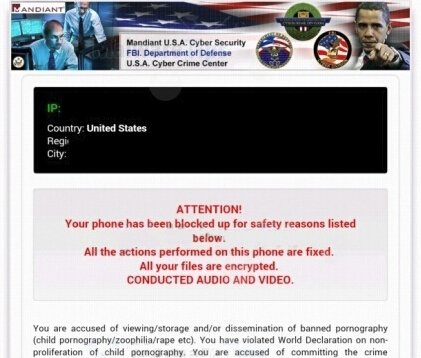
- Mandiant U.S.A. Cyber Security scam free removal steps:;
- Apple Footer;
- Krebs on Security!
Network Computing Dark Reading. About Us.
In-depth security news and investigation
Follow DR:. Tech Library. Black Hat News.