To figure out the target's Mac password without changing it, the hash will need to be brute-forced and cracked. MacOS does an excellent job of securing the target's password. It's not possible to view user passwords in plain-text. CPU-based cracking solutions like JohnTheRipper will literally take decades to crack a single hash and are therefore not effective.
Hashcat with a decent GPU is highly recommended. To access recovery mode, first, make sure the target MacBook is fully powered off. If the below screen appears, recovery mode was enabled successfully and readers can proceed to the next step in this tutorial. If the MacBook requests a password, it means the firmware is protected and configured to prevent recovery mode attacks. Unfortunately, this means the target MacBook isn't vulnerable to the attack shown in this article. It even prevents root users from changing and accessing select directories.
To find out if SIP needs to be disabled, open a Terminal while in recovery mode.
In the menu bar at the top of the screen, select "Utilities," then "Terminal. If the output returns many. If the output returns "Operation not permitted," disable SIP using the below csrutil command.
After the restart prompt appears, shutdown and boot into recovery mode again. With SIP disabled, it's safe to proceed to the next step in this tutorial. Wait a few seconds to allow it to auto-mount.
Full screen Cracking view
Then, copy the desired. The target. In that case, the hard drive name may appear as "Macintosh HD" or some variation. That's it. The necessary file has been extracted, the target MacBook can be shut down, and the remainder of the tutorial requires a separate MacBook owned by the attacker. If SIP was disabled in the previous step, re-enable it before shutting down with the below command.
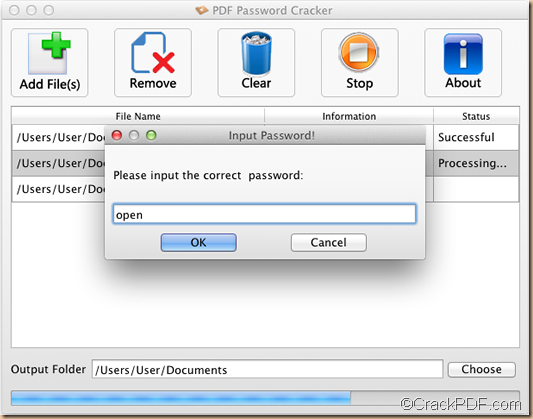
As long as the target's. The Python script used to convert the extracted. Open a Terminal and download the hashdump script with the following curl command. The -o argument will save the script with the "hashdump. Then, give the script permission to execute using the chmod command. Remove text surrounding the hash shown below and save it to a file called "hash. To crack the target's hash with Hashcat , use the below command. The dictionary attack, or "straight mode," is specified using the -a 0 argument.
Top 3 Mac Password Reset Software
The macOS-specific hashing mode is enabled using the -m argument and is required for all macOS hashes extracted from version Nevertheless, to prevent this kind of things it is good to have a Cybersecurity Professional. But the fact is, there are many vulnerable websites one can force into with the help of password hacking software.
Similarly, password cracking is a process of recovering or guessing the password from data transmission system or stored locations. It can be utilized to retrieve a forgotten password or get a password for unauthorized access. The big software firms usually use it to check the security of their applications in penetration testing. These password crackers also are proof that your password can be hacked too. The programmers have developed a good number of password cracking and hacking tools, within the recent years.
Just like any other thing on the planet, each tool has its very own pros and cons. However, down here I prepared you 15 top password tools for both recovery and hacking.
- impresora samsung ml-2165w laser wifi usb 20ppm windows mac?
- Navigation.
- scan your mac for errors?
We do not promote unethical or malicious practices at any rate. This fantastic program is one of the top password cracking tools when it comes to brute force attack. This tool is not designed to identify the right response; such as hitting and catching passwords or usernames. More precisely the content of the baseline and the content of the response, and then they are compared to generate end-results. This software is usually used for penetration tests and created to support protocols which are not supported by other kinds of brute forcing tools.
Download link: Crowbar. The Aircrack works with a wireless network interface controller which has a driver that supports raw monitoring mode. Also, it can sniff the traffic from Another new attack was included by a team from the Darmstadt Universty of Technology. Given that, it has the purpose to decrease the number of initialization vectors IVs. They are essential to decrypt a WEP key in the 0. This free password cracker analyses the encrypted password packets at first and then breaks the passwords using its stealthy cracking algorithm.
This cool tool is focused more on Wifi security where it does monitoring that captures packets and exports all the data into text files for processing by the third-party tools. Moreover, it handles fake access points, de-authentication, and replies to attacks using the packet injection. Aircrack password cracker free download: Aircracker-ng.
What are the Best Password Cracking tools? (updated for ) | Networking and Security
L0phtCrack is a password cracker and recovery program. It is a perfect password cracker for Windows 7 and also for other windows systems. It works by obtaining the hashes from stand-alone primary domain controllers, networked servers, Windows workstations and Active Directory. L0phtCrack has many ways of generating the password guesses, and hence, is a standard tool for cracking windows passwords.
The program utilizes rainbow tables, dictionary attacks, hybrid and brute force attacks. It also has a schedule routine audit functionality that lets you perform the password scans at a time which is convenient for you. There are three different versions of it from which you can choose, the three versions of L0phtCrack include Administrator, Consultant, and Professional edition.
Mostly, this software is used to recover lost Microsoft Windows passwords. L0phtCrack download link: L0phtCrack. Ophcrack is one of the top rainbow-tables based password cracker. You can crack windows computer passwords with it, within just a couple of minutes. Ophcrack does not leave any traces behind it as the app is available as lie CD. You only use it on the target computer and then take out — simple. The primary purpose of this password cracker is discovery. If the password is a simple one, it can find that out within a few minutes.
Download link: Ophcrack. It is a hugely parallel, modular, speedy and login brute-forcing tool. Please note that you will need to learn commands before using it since Medusa is the command line tool. Some of the essential features of this password cracking software are:. This tool has the focus on cracking passwords using brute force attacks.
Medusa is one of the very few parallel password cracking tools that are available on the market. Mean, it can perform simultaneous attacks where you can crack passwords of multiple email accounts for example at a time rather than just one.
Best PDF Password Cracker for Mac OS X
Besides this, it can carry fast attacks over a large number of protocols which include a database, https, telnet, HTTP, and smb. Download link: Medusa. FSM or known as SolarWinds Firewall Security Manager is a best-suited security solution for companies and organizations that need reporting and management of their security devices.
Both, the configuration and set-up of this tool are straightforward — and you can add multiple clients to grant various administrators access to the system. No, you will need to pay for it — but it has a free trial though. A well-known company offers the tool and the firm also provide many other security-related programs. Some of the uses of this tool include router password decryption, network discovery scanners, TCP connection reset program and SNMP brute forcing cracker. Download link: SolarWinds. This tool supports multiple techniques and methods to expose the vulnerabilities of the targeted web application.
With Wfuzz you can audit the parameters, discover unlinked sources like directories, files, header, etc.