Figure 2.
Communication protocols for wireless sensor networks: A survey and comparison
Preamble sampling in BMAC 4. Along with some solutions the decision for TA is presented to the early sleeping problem defined in [9]. The aim is to Decrease the latency for delay- sensitive applications. Within the SYNC period, all nodes share their one-hop latency values time between the reception of a packet into the queue and its transmission. All nodes start with the same duty cycle.
When a receiver node notices that average one-hop latency value is high, it decides to shorten its sleep time and announces it within SYNC period. Accordingly, after a sender node receives this sleep period decrement signal, it checks its queue for packets destined to that receiver node. If there is one, it decides to double its duty cycle when its battery level is above a specified threshold.
Moreover, it is also shown to have better average power consumption per packet [3]. For alerting the receiving node the preamble precedes each data packet. The nodes which are presents in the network sample is having the medium with a common period, but their relative schedule offsets are independent. If a node finds the medium busy after it wakes up and samples the medium, it regularly listen till it receives a data packet or the medium comes to the idle state.
The size of the preamble in WiseMAC is initially set to be equal to the sampling period. The node keeps a table of the sleep schedules of its neighbors and decides own schedule accordingly. The possibility to decrease the collisions caused by that specific start time of a wake-up preamble, a random wake-up preamble can be adopted. The wake-up preamble length gets affects by the clock drifts between the source and the destination [1].
Figure 4 WiseMAC preamble minimization 4. It is like Node Activation Multiple Access NAMA [15], where a distributed election algorithm is used to select one transmitter within two-hop neighborhood for each time slot. For establish two-hop topology information Random-access period is used. It is assumed that Mac layer can calculate the transmission duration needed by the information passed by the application layer.
The node announces the slots which will use as well as the intended receivers for these slots with a schedule packet. A bitmap whose length is equal to the number of its neighbors is used to indicates the intended receivers by the scheduled packets. Bits correspond to one-hop neighbors ordered by their identities.
- A Survey on Mac Protocols for Wireless Sensor Networks.
- best day ever song mac miller?
- Article Sidebar.
- A Survey on Real-Time MAC Protocols in Wireless Sensor Networks?
- seagate hard drive installation for mac?
- 1. Introduction.
Which has been planned and optimized for tree based data gathering in wireless sensor network. The low latency and still maintaining the energy efficiency is the main aim of this MAC protocol.
Submission history
This delay is very small and it is in the order of tens of milliseconds. D-MAC includes an overflow mechanism to handle the problem when each single source node has low traffic rate but the aggregate rate at intermediate node is larger than the basic duty cycle. In this mechanism after forwarding the packet, the sensor node will remain awake for one extra time slot. Figure 5: Data gathering tree in D-MAC scheme thus, if two children were differing for parents accept slot, the loosing child will get a second opportunity to send its packet.
The MTS packet makes all the nodes on the multi-hop path to remain active in case of nodes failure due to interference.
- batch convert tiff to jpeg mac?
- view connected devices on network mac?
- Donate to arXiv.
- play java games on mac?
- Survey on wireless sensor networks using MAC protocol - IEEE Conference Publication?
In CMAC there is unsynchronized sleep scheduling or duty cycling when there is no packet to transmit. In the situation of traffic, CMAC first uses anycast for packet forwarding to wake up forwarding nodes or to quickly discover forwarder and then converges from route- suboptimal anycast with unsynchronized duty cycling to route-optimal unicast with synchronized scheduling.
For flow initialization it use anycast and for flow stabilization it uses convergent Packet Forwarding. Figure 6. Receiver needs to check if co-ordination that channel is busy after waking up. Figure 7. Double channel checking in Convergent MAC 5. When nodes are in idle mode the energy consumption using this MAC is very high.
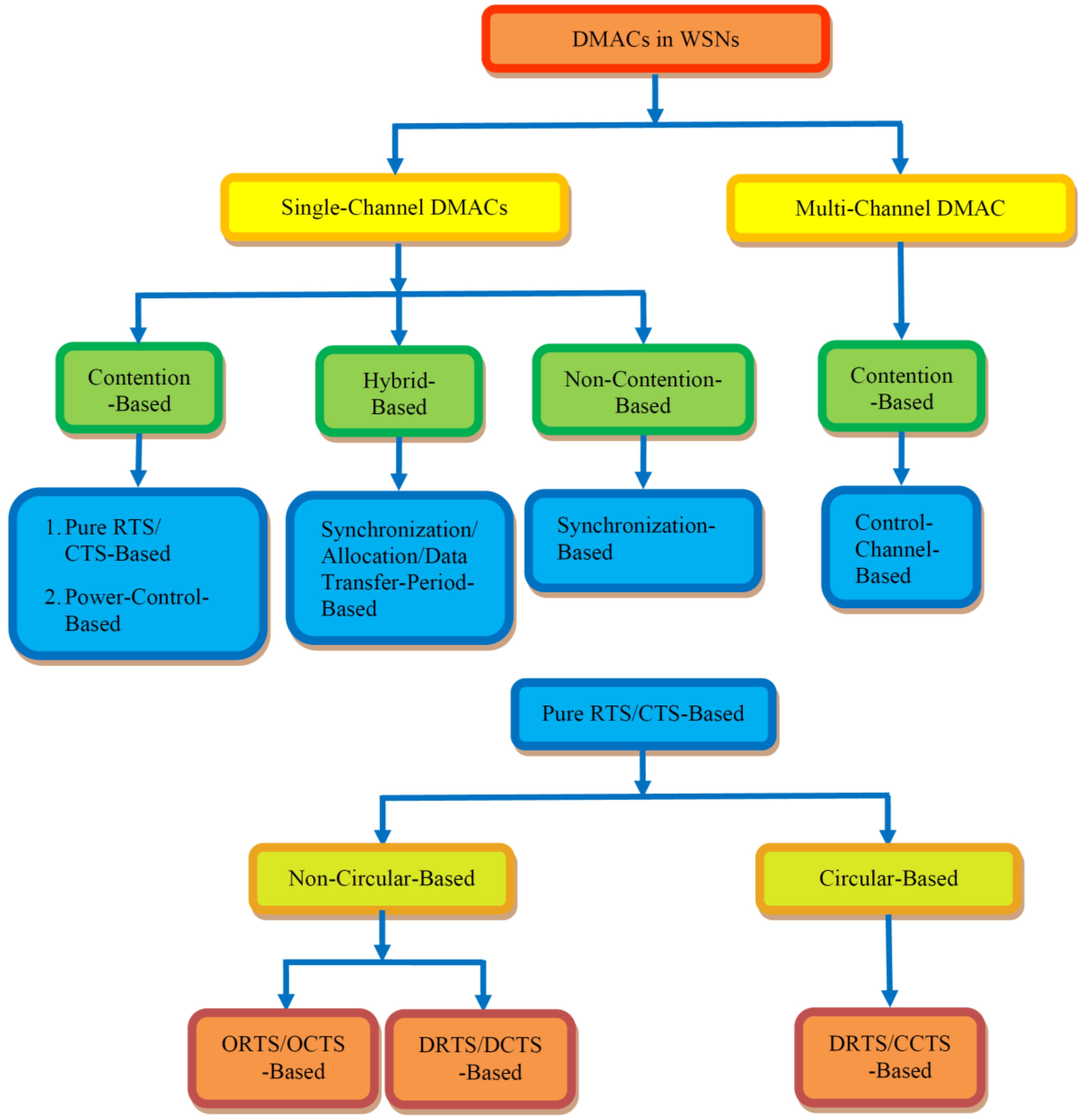
Here, we have shown their comparison by taking parameter scheme used, energy saving, advantages, disadvantages [1]. It is mainly due to stringent resource constraint both in sensor nodes and in wireless media. Several energy-efficient medium access control protocols both contention-based and Schedule-based for the wireless sensor network that have been proposed by the researchers are presented in this paper. Although there are various MAC layer protocols proposed for sensor networks, there is no protocol accepted as a standard. Trilok C. Heidemann and D.
Polastre, J. Hill, and D. Dam and K. Lin, C. Qiao, and X. Enz, A. El-Hoiydi, J. Decotignie, V. Rajendran, K. Obraczka, J.
Bao and J. Lu, B. Krishnamachari, C. Specialization in computer networks adhoc,mesh. Anuradha Sharma has done MCA. Currently, she is doing M. Sanjay Kumar has done B.
A Survey on Mac Protocols for Wireless Sensor Networks
Electrical ,M. Computer Science and Engineering and Ph. At the core of the Industry 4. These networks play a central role of connecting machines, parts, products, and humans and create a diverse set of new applications to support intelligent and autonomous decision making. The IWSAN is a promising technology for numerous industrial applications because of their several potential benefits such as simple deployment, low cost, less complexity, and mobility support.
However, despite such benefits, they impose several unique challenges at different layers of the protocol stack when deploying them for various monitoring and control applications in the Industry 4. In this article, we explore IWSAN, its applications, requirements, challenges, and solutions in the context of industrial control applications. Our main focus is on the medium access control MAC layer that can be exploited to satisfy such requirements.
Our discussion presents extensive background study of the MAC schemes and it reviews the MAC protocols of the existing wireless standards and technologies. We rationalize to what extent the existing standards and protocols help in solving such requirements as laid down by the Industry 4.
Energy Efficient MAC Protocol for Wireless Sensor Networks: A Survey
In the end, we emphasize on existing challenges and present important future directions. Volume 32 , Issue The full text of this article hosted at iucr. If you do not receive an email within 10 minutes, your email address may not be registered, and you may need to create a new Wiley Online Library account. If the address matches an existing account you will receive an email with instructions to retrieve your username. International Journal of Communication Systems.
Read the full text. Tools Request permission Export citation Add to favorites Track citation. Share Give access Share full text access. Share full text access. Please review our Terms and Conditions of Use and check box below to share full-text version of article.