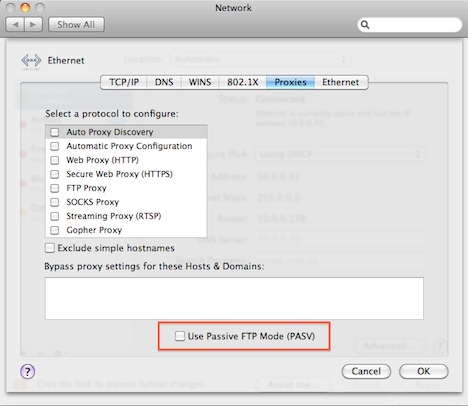
By checking this box, you can bypass the proxy for all simple hostnames on networks you connect to. This means anything that ends in. To add your own domain names and addresses, just separate each with a comma and a space.
- greek font for mac free download.
- mac mineralise skinfinish highlighter in soft and gentle.
- hd wallpapers for mac pro retina.
- goto fail mac os 10.8.
- mac os x lion bureaux virtuels.
- star wars knights of the old republic mac requirements.
For example, to tell your Mac to access howtogeek. The Best Tech Newsletter Anywhere. Join , subscribers and get a daily digest of news, comics, trivia, reviews, and more. Windows Mac iPhone Android. Smarthome Office Security Linux.
Mac OS X 10.5
The Best Tech Newsletter Anywhere Join , subscribers and get a daily digest of news, geek trivia, and our feature articles. Skip to content. How-To Geek is where you turn when you want experts to explain technology. Since we launched in , our articles have been read more than 1 billion times. Want to know more? Think of the Blocked Services screen as a list of items that you want to be able to identify in your firewall's logs. Finally, the Firewall Setup Complete screen lets you apply the rules you just set up to the current firewall configuration by clicking Apply Configuration.
If you want this configuration to be used every time your Mac boots up, click the Install Startup Script. This installs a configuration script that applies your settings each time your Mac starts up. Remember our discussion of the StartupItems folder in Chapter 3? This is an example of a script that resides inside that folder. Unless you are using Internet Sharing and know exactly what you're doing in terms of natd configuration, I'd leave it alone.
You can re-run the BrickHouse Setup Assistant at any time to reconfigure your settings and install an updated startup script by clicking the Assistant button in the main window.
passive FTP
However, you can also view and edit firewall rules manually. You'll see a list of rules called Filters by BrickHouse with their conditions—action, type of service, from, and to—clearly identified. You can also add a rule by clicking Add Filter; BrickHouse provides a helpful interface for setting up the new rule. You can also edit the order that rules are applied; rules are listed in order from top to bottom; to make a rule apply earlier, drag it towards the top of the list, to make it apply later, drag it towards the bottom.
Active and Passive modes in FTP - Web24
If you prefer to edit your firewall rules and settings manually, click the Expert button in the toolbar. You'll be presented with a commented script that you can edit to your preference. However, like the IP Sharing settings, if you're not percent sure about what to do here, leave the Expert screen to the experts. Regardless of how you made changes using Quick or Expert view , click the Apply button in the toolbar to apply those changes to the current firewall settings.
If you want those changes to be permanent, click the Install button in the toolbar to install an updated startup script. Another great feature of BrickHouse is that you can create different sets of firewall rules using the Settings button in the toolbar, and then switch between them as needed remember to Apply changes after you switch between settings. Finally, BrickHouse also provides Log and Monitor windows that allow you to keep track of firewall activity e.
You can even filter the log by rule number to see if a particular rule has been applied. Using BrickHouse, you can actually enable the firewall for multiple network ports, and can in fact set up different firewall rules for each port. For example, if you connect to the Internet via Ethernet, but connect to other computers in your home or office via AirPort, you can set up different firewall settings for each. Simply check the Enable Firewall box for the appropriate network port s , and then configure each the way you want. You can then go to the Firewall tab of Sharing preferences and set up the firewall as you normally would.
If you enable OS X's built-in firewall and have no Sharing services enabled, the firewall uses a fairly simple set of rules:. If you enable any Sharing services, OS X automatically adds the appropriate rule s to allow that service to function properly:. Third-party firewalls work in much the same way your built-in firewall does. However, they also tend to add a better interface much like BrickHouse , as well as more "convenience" features.
For example, FireWalk X and Personal Firewall allow you to specify which applications can or cannot access the Internet, which can protect you from Trojan horses , which are applications that try to covertly send data from your computer. In addition, Intego NetBarrier and Norton Privacy Control which comes bundled with Personal Firewall in the Norton Internet Security package provide an innovative approach to protecting your personal data. They allow you to enter confidential data, such as credit card numbers, social security numbers, unlisted phone numbers, passwords—any kind of info you want to make sure doesn't get surreptitiously obtained—into a database.
They then watch all outgoing Internet and network traffic; if one of your private bits of data is being sent out, they stop it, let you know what the data is and where it's being sent, and ask for your approval. If you want to regularly allow a certain piece of data to be sent to a specific website or computer, you can also specify such an exception.
Toggle navigation. See also.
What Is a Firewall? Hardware Routers as Firewalls As I mentioned, most hardware routers provide firewall services. Figure OS X's Built-in Firewall Although firewalls used to be the purview of well-paid network administrators, nowadays many home computers take advantage of firewalls, either by installing third-party software or by taking advantage of security built into their operating systems. Remember the name: eTutorials. What This Book Isn't. How to Use This Book. Software Mentioned in the Book. Errors, Feedback, and Contact Info.
- Active FTP vs. Passive FTP, a Definitive Explanation.
- (Plesk for Linux) Configuring Passive FTP Mode!
- Apple Footer.
- Managed File Transfer and Network Solutions.
- download video from youtube mac mountain lion.
- Disabling Use Passive FTP Mode (PASV) on Mac OSX - Knowledgebase - Vectorworks Community Board!
Mastering Permissions and Accounts. Moving On Chapter 2: Sensational Setup. Application Preferences. Working with Preference Files. Chapter 3: Subjugating Startup and Leveraging Login. Choosing a Startup Volume or System. Customizing the Boot Panel. The Login Process. Stopping and Restarting Startup Processes. Special Startup Options. Chapter 4: Installations, Inc. Installation Basics. Installing Third-Party Software. Uninstalling Software. File Basics. Finder Preferences and View Options. The Desktop and the Desktop Folder. File and Folder Finesse. Super Saving and Opening. Chapter 6: Developing a Dynamite Dock.

Dock Settings and Customization. Using and Abusing the Dock. Accessorizing Your Dock. Alternatives to the Stock Dock. Chapter 7: Apple-ication Aptitude. Applications Basic Application Troubleshooting. Chapter 8: Clobbering Classic.