Figure 2. Traffic patterns click the image to enlarge. One can observe that the second call sends a POST to ausumeetings[. Stage 2 involves downloading a PE file. It is downloaded as Cormac. Figure 3. Observed processes click the image to enlarge. Once the malware is executed, it will drop the Stage 3 DLL file with filename api-ms-win-downlevel-profile-l To load the malware, it executes rundll It bears stressing that we do not encourage using the data presented above as IOCs for your own analysis.
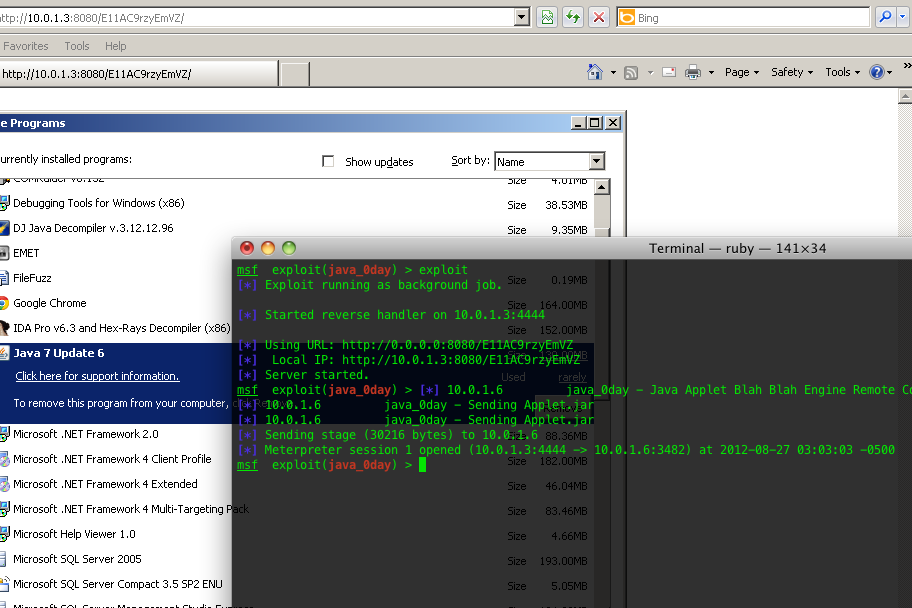
After assessing the samples multiple times, each network traffic infection sequence appeared to be different, no matter what sequence of testing was performed e. After detailed network forensics of the traffic, it was determined that no single stable URL path or URI query component URI path component, file name, or URI query parameter showed a consistent pattern either same entry nor regex definable pattern , and further reverse engineering was required to determine the methods used to achieve this.
As a result of this additional analysis, it was determined that the URI path is a random generated string with the following pattern:. The encoded data contains the following system information of the infected machine:. After sending the encrypted data it will wait for a reply which is encrypted by the same algorithm above. Based on our investigation of Operation Pawn Storm, we know that the infection happens in two stages:.
This fourth stage malware is expected to be an encrypted executable file. A number of victims were identified during the course of our investigation.
Please review our terms of service to complete your newsletter subscription.
The targets are in the United States or Canada, and those we were able to identify via IP are big defense contractors, as typical for Operation PawnStorm. Trend Micro is already able to protect users against this threat without any necessary updates.
Our Browser Exploit Prevention detects user systems against exploits targeting browsers or related plugins. Vulnerability protection in Trend Micro Deep Security protects user systems from threats that may leverage this vulnerability with the following DPI rule:. For browser-specific instructions on disabling Java, click here. If you must use Java, security experts are prepping an unofficial patch for the program that should blunt this vulnerability, but it is being offered on a per-request basis at this point. A number of experts I know and respect have vouched for the integrity of this patch, but installing third-party patches should not be done lightly.
If you do not need Java, get rid of it, and if you do need it for specific applications or sites, limit your use of Java to those sites and applications, using a secondary browser for that purpose.
How to Stop the Java Zero-Day Exploit | Sophos Security Tips
Tags: 0day , Andre M. You can follow any comments to this entry through the RSS 2. Both comments and pings are currently closed. Brian, I have Java 6, version Does it help if we use limited user accounts? I would strongly encourage you to adopt the approach I recommend in this column: If you do not need the program, get rid of it. Then, use the secondary browser only for those sites that require Java. Before dabbling with SRP, set a System Restore point in case you paint yourself into a corner with it.
Thanks for this mechBgon! Why is not mentioned anywhere about the effectiveness of an anti-executable approach in preventing the payload from executing? Thanks for the warning. Neither of these two updates included security fixes. More here:. A slight modification to my post.
blog archive
Oracle patches Java every 2 months, with security fixes provided every 4 months and non-security bug fixes and enhancements provided every 4 months. There is an approximate 2 month lag between security updates to Java and non-security updates to Java as shown at Wikipedia:. That is because the devs use Mac OSX and vmware to test exploits on victims in a virtualised environment.
I included it in this post for convenience. Mostly use Chrome now.
Do I breath a sigh of relief or do a long-needed audit of my personal machine? Just note that 1 most but, not all popular Linux distros use Firefox as the default web browser and 2 the only Linux distro that I am aware of that includes the NoScript add-on by default is the U. To be safe, I would assume that it does until I hear otherwise.
I appreciate it. A friend of mine also told me that NoScript should prevent it. I realize that this a question which may go beyond the scope of your column, but it arises each time that I read about a new zero day exploit. But I would not count on that to stop attacks against a zero-day in Java itself. EMET is designed to prevent memory corruption exploits or their shellcode from running. I agree. Update the main image periodically.
Use snapshots. Either rollback after a suspected incident or load from last safe snapshot before doing a sensitive application. This forces the typical hackers to use social engineering or try to find flaws in the sandboxing scheme. Obscurity always helps too. Something to remember. These sandboxes are supposed to make exploits against the software they protect impossible or at least significantly harder to pull off. The reality is that every security sandbox developed so far has fallen under hacker attention. He said over holes perforated the sandbox. Can he back that up with hard data compared to non-sandboxed alternatives?
Several weeks ago I got sloppy, and unlucky. Long story short, I ended up having to do a partition restore to get rid of what was biting me. Professionally I have been a Java developer for over 10 years. I do not have Java enabled in any browser on any operating system.
Turn off Javan in all of your browsers and I doubt you will ever need to turn it on again. I agree, I too develop java for 7 years and though I keep Java installed and up to date on my home laptop, I hardly ever found the need for it on the browser. Both IcedTea 2. Easiest solution is to remove Java altogether from your system.
- New Java Zero-Day Exploit Shows Multi-Platform Development.
- photostream not working on mac?
- mac upcoming collections 2020 temptalia?
Problem solved. Java is very much alive on servers. Closure is also bringing it back on the client. Enterprise, production quality too people!
Otherwise, why would they use it? Since Java was developed at least partly for the Web, I am surprised at how few Web sites need it. I would like to second PC. My users require Java for everyday work, our call center app uses it for one. Detaching Java from IE would be nice, but is not an option at the moment.
Aparently it only exploits Java 7. I tried to exploit Java 6. But you can bet people are working on it.
Zero-Day Exploit Alert: Flash, Java
They need a few visits from American Special Operations Forces if they think everything should be legal. I recently reinstalled Windows I had nothing better to do and took your advice and have not installed Java. Only sites I know of that are critical for my workplace environment are a couple government websites.
This time. But I always keep the browser plug-in disabled until needed. I installed java7 on my Mac and it no longer works in Chrome, which is my main browser. That was a lucky coincidence. So, no mass Flashback type problem for basic users, right? Does the vulnerability affect me? Agree with the noscript and scriptno plugins mentioned already, as well as the methods for disabling java.
